How Recare protects the health data of 300 000 patients? 🏥

Created in 2016, Recare is a solution that coordinates patient transfer requests between hospitals and healthcare facilities. Example: between emergency rooms and MSO (Medicine, Surgery and Obstetrics) facilities.
Present in France 🇫🇷 and in Germany 🇩🇪, the Recare solution:
- Reduces the Average Length Of Stay (ALOS) in the facilities
- Saves time for medical and administrative teams
- Centralizes all transfer requests on a single platform
The Recare problem
For Charles Cote - CTO @Recare, the confidentiality of medical data is its main imperative. He wants to implement the highest level of confidentiality on the data.
Here are the different issues he wanted to address:
- Guarantee that only healthcare professionals can access data (not even Recare or its host).
- Prevent data from being stolen even in the event of unauthorized access to Recare's servers.
- Sleep well 😴
End-to-end encryption was chosen by Charles Cote to address Recare's issues. It is a technology that ensures that only authorized users will be able to access the data, and not hackers, administrators, institutions, hosts, or even Recare. In other words, it prevents data from being stolen even if there is unauthorized access to Recare's servers.
This technology is much stronger than encryption in transit combined with encryption at rest.
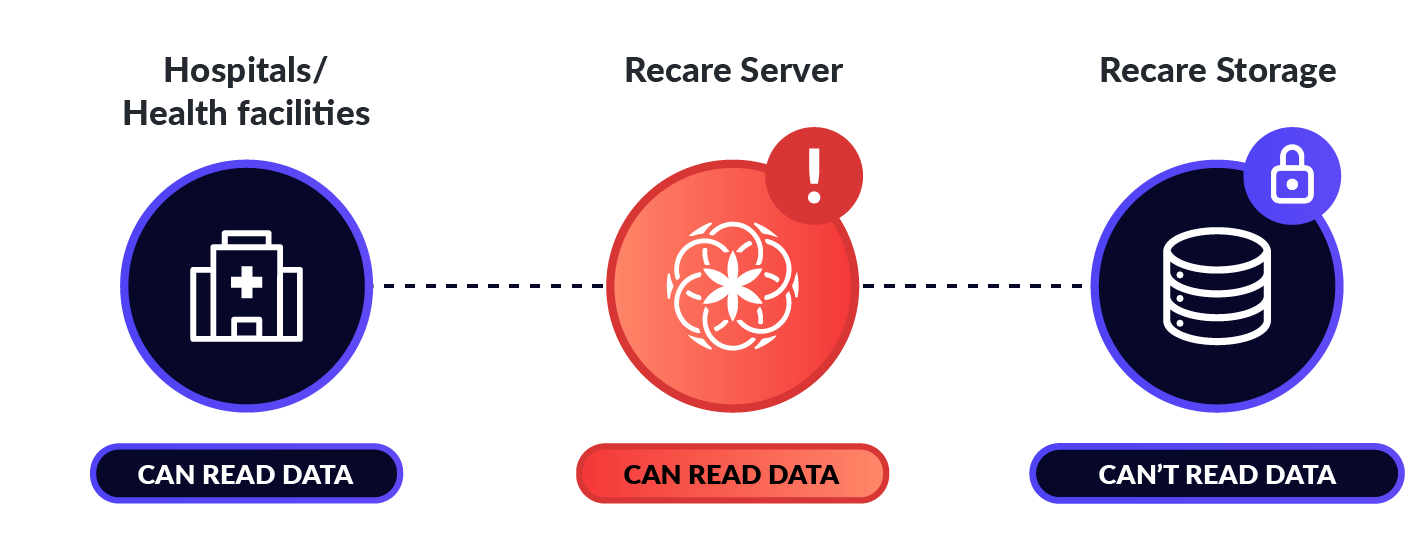
Without End-to-End encryption:
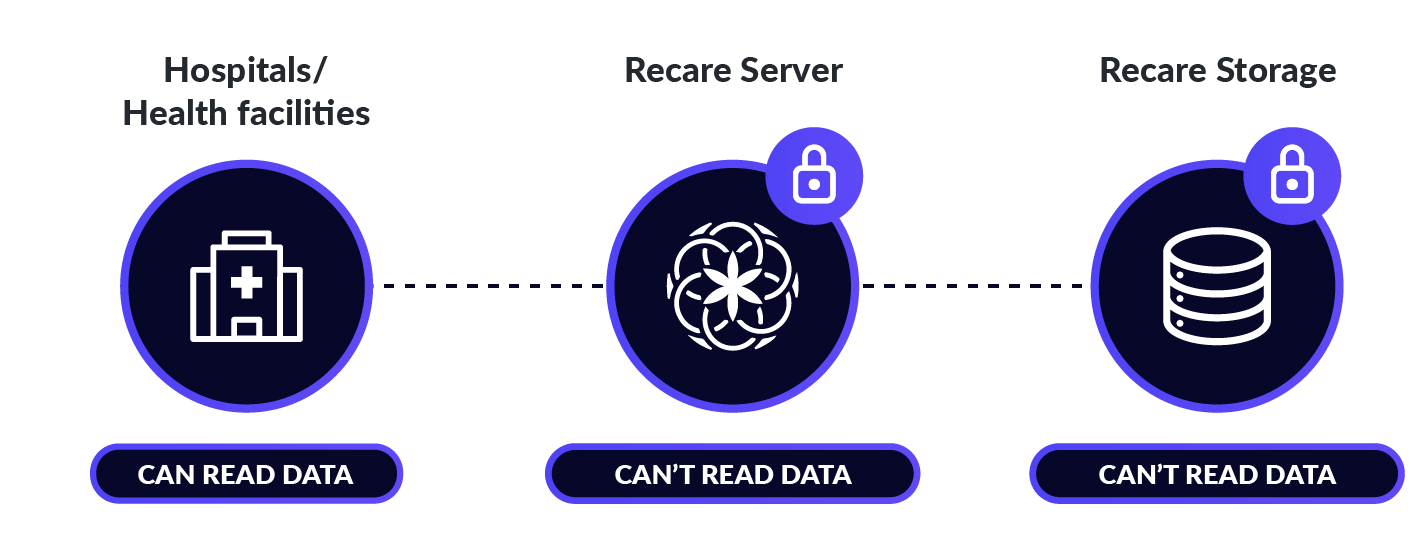
With End-to-End encryption:
How does Seald help Recare solve its problems?
In March 2021, Charles contacted Seald for support in integrating end-to-end encryption.
At that time, Recare already had an end-to-end encryption implementation, developed in-house with open-source libraries, and implemented very early in the life of their product.
After an audit revealed that the in-house implementation was not state-of-the-art, Charles turned to an external solution like Seald for several reasons:
- It relieves Recare of internal maintenance and auditing of a complex tool, allowing them to focus on their core business.
- It assures Recare that the encryption protocols used are state-of-the-art.
- It allows to demonstrate to its customers the physical inaccessibility of the data by Recare (which is always arguable when the solution is internal).
Seald steps in by offering an end-to-end encryption SDK "as-a-service" for developers to help them protect their users' data with absolute confidence, without any need for cryptographic skills.
Private key storage 🔐
In the original implementation of Seald in Recare, each user could retrieve one of their private keys:
- In the browser storage if the user authenticated to that browser.
- With a recovery mechanism where the user has to copy an OTP (one-time password) received by email.
Logically, once authenticated in a browser, a user does not need to re-authenticate unless the browser cache is cleared.
The problem Recare faced was that many of its customers have an IT policy of resetting browser caches every day... so some users had to be emailed an OTP every morning to use Recare: it was unusable as it was.
To overcome this problem, Recare offers another silent recovery mechanism: the password. The password is used to encrypt a private key and this encrypted private key is saved remotely.
The recovery mechanism where the user has to copy an OTP (one-time password) received by email is then used only as a last resort, when the user has forgotten their password and wishes to reset it.
Caching of symmetric keys 🔑
When Recare integrated Seald, symmetric key caching was not offered. This caused each decryption to trigger a network request, which in their case could slow down page loading.
The reason why caching was not implemented at the time, and is still not enabled by default in the latest SDK versions, is that it prevents instant revocation of access to a key: the key will remain accessible to someone who is revoked for at most the TTL of the cache.
We have made 2 changes:
- In v0.14.0: implemented serialization and reinstantiation of symmetric keys to allow manual cache creation.
- In v0.16.0: implemented an optional cache, by default in memory only, but customizable to allow a persistent cache implementation.
Group management 👫
The integration of Seald into Recare is centered around the functionality of groups.
Each care facility is represented by a Seald group, and every professional in a care facility is a member of that group.
When a patient record is sent from one facility to another it is encrypted for both the sender group and the target group, and the sender group is declared as the "managing group" so that each member of the group can manage the rights to that key.
There are also some cases where the group is not yet created at the time the file has to be encrypted (this can happen the first time a care facility receives a patient file).
In this case, strictly end-to-end encryption is technically not possible, but it can be approached: the record is encrypted for an UnregisteredUser, which stores the bare symmetric key on the Seald servers in escrow, and when the group is finally created, the Recare server assigns that UnregisteredUser to that newly created group, which triggers the Seald servers to encrypt the symmetric key for that group.
In this scenario, Recare never has access to the key, and Seald never has access to the data.
Benefits of Seald within Recare
With Seald, Recare goes beyond traditional data security practices. End-to-end encryption ensures that only authorized users will be able to access medical data, greatly reducing the impact of a potential data leak 🛡️.
A malicious actor who managed to infiltrate Recare's servers would not be able to access the data. This is a robustness that a hosting provider certification (HDS, ISO 27001, HIPAA, etc.) for health data hosting does not offer.
It is by ensuring this higher level of data confidentiality that they can gain and keep the trust of their customers in France and in Germany.
Finally, Seald allows Recare to guarantee to its users to always be at the forefront of security, and to follow the evolution of technologies in this field.
Seald is the only certified end-to-end encryption SDK in the world. The solution is certified by the ANSSI (the French cybersecurity agency). The technology has been audited by third-party experts, based on compliance analysis and advanced penetration testing, ensuring Recare has a robust security model.
As always, feel free to contact our team for more information.
See you soon 👋
